Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
So a little bit of preamble is probably necessary as this is my first “soapbox” post. Throughout my career I have found small nuggets of information that have evolved into “truths” in my mind. These truths continually reappear in my personal and professional life and I tell everybody about them. One of these truths is “The Four Problems.”
It is my truth that only four types of problems exist in the world, and these Four Problems appear everywhere, even in cyber security. I also believe that each of these problems has an approach that enables you to solve that specific type of problem. Notice that I didn’t say solution because the solution is something that we need to figure out, leveraging the approach that helps address each of the four problems individually. Why is problem solving important for a Cyber Governance function? In order for us to accomplish our mission, we must not only point out when improvements are necessary, but also to help drive the solution.

Ok, so enough with the explanation…what are the four problems then? VUCA is a military acronym that explains problems that are volatile, uncertain, complex, and ambiguous. While VUCA is elegant and seems straightforward, I’ve seen professionals from all industries leverage it incorrectly. Given the difficulties faced within our industry, I’ll walk you through The Four Problems, provide real-world examples of each, and how to solve for them in your day-to-day activities. Let’s begin!
It’s become a trendy managerial acronym: VUCA, short for volatility, uncertainty, complexity, and ambiguity, and a catchall for “Hey, it’s crazy out there!” Source: HBR.
Below is a decision matrix which can help you diagnose the four problems. The matrix is based on two different variables: the amount of information that you know about a particular situation (low or high) and how well you can predict the outcome of your actions (low or high). Cyber security professionals have been taught to leverage quantitative thinking and to throw out qualitative thinking, but in this case simpler is better.
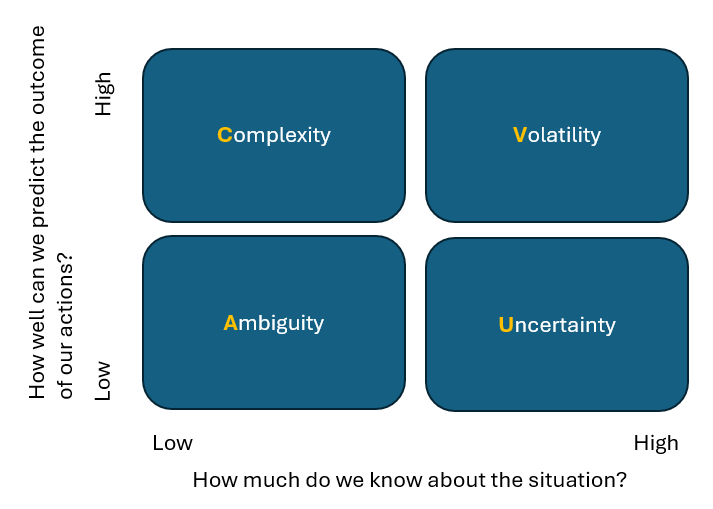
When a volatile problem presents itself, we will understand the situation and will have a high degree of confidence in the solution. With that being said – it is difficult to predict the timing, magnitude, and duration of a volatile problem. The best approach to solve a volatile problem is to invest in solutions that improve resilience of the business process. As these solutions tend to be resource intensive, make sure that you only develop solutions for the most critical services.
When I first encountered VUCA, I asked myself “what kind of approach is this and how will it help me”? It forced me to change how I look at problems and once I used this approach, it became clearer. A good cyber security example for volatility is a cybersecurity incident such as ransomware. Ransomware is a known attack type and while we know how to recover from it, we can’t predict when or how bad the incident will be.
As organizations planned for ransomware, they progressed through what I call the “recovery” maturity evolution. Initially, they backed up data to create a “cold backup” paradigm. Subsequently, they implemented improvements to that paradigm by testing and protecting it. Eventually, they reached the point where hot protected backups were available for the most important business services. While very effective, these solutions can be very resource (personnel, budget) intensive but they can help mitigate the length of an outage and can sometimes prevent organizations from paying ransoms.
An uncertain problem is one where we know a lot about a situation, however we are not very confident in predicting the outcome of our response. This is most often a situation where there is a lack of knowledge. Where a volatile problem can develop rapidly and the magnitude can vary significantly, an uncertain problem is different. This is because while we know alot about the situation, we are unsure how our actions will affect the outcome. The most effective way to address problems of uncertainty is to improve the level, source, and quality of information you know about the problem. Often you will need to reach outside of your organization in order to acquire, interpret, and leverage this information.
An example of an uncertain cyber security problem is threat intelligence. Threat intelligence seeks to close gaps in our understanding of our adversaries’ techniques, tactics, and procedures and their goals.
At first, cyber security organizations stood up their threat intelligence solutions internally, identifying adversaries and their tactics without outside help. Over time, insights from traditional fraud and counterterrorism teams showed that access to outside data helped break the cycle. Organizations like FS-ISAC is an example of an Information Sharing Analysis Center (ISAC) focused on supporting the financial services industry. Chances are, there is an ISAC available for you to join. Find a list of the member industry ISACs at the National Council of ISACs website. There are also third parties who sell threat intelligence services and integrate their feeds with cyber security technology providers.
Complexity is often the hardest problem for a cyber security or technology professional to diagnose and solve. Complexity is characterized when you think you know a lot about the problem, but in reality data volume, veracity, validity, and/or velocity makes it difficult to understand the real problem. You will have a high degree of certainty in your solution fixing the problem, but unforeseen consequences often develop. Why is this type of problem is the hardest to solve? It is because we mistakenly believe that not enough data is available – thereby aggravating the problem. The solution is to do the exact opposite – reduce the number of material variables and simplify the solution.
A classic example of a problem in complexity is vulnerability management. This process becomes complex due to daily discovery of new vulnerabilities and the ever-changing technology environment. On top of that, we try to add more information and unintentionally make the process more complex.
Organizations that master vulnerability management simplify as much as possible, creating roles to identify new problems before they become systemic. Instead of adding data to reports, effective organizations leverage that same data to filter reports by organization to reduce effort. Best in class teams will identify patch deployment failures, identify root causes, and automate error detection and correction routines.
Ambiguity is a difficult problem because all of our questions are unanswered. We know the least about the risk situation, and there is little confidence that a solution will actually be effective. So little is known about these types of problems (or risks) that it is generally believed that they are unsolvable. Cyber security professionals usually look at these types of problems, panic and just say “no”. This approach tries to stonewall the risk completely, even when using the technology seems promising from a business perspective. Problems of this flavor are most thoroughly solved through experimentation, rapid prototyping, and scenario building. This approach quickly creates an understanding of the risk profile and how to manage the new risk.
The timeliest example of an ambiguous problem is artificial intelligence, or AI. AI, like cloud computing before it are revolutionary technologies that are fundamentally changing how organizations operate their businesses.
While AI is not the only technology that risk management leadership has flat out said “no” to, think back to each time this answer was provided by the cyber security team. While I’m picking on my own industry, organizations including legal, risk management, regulatory compliance, and privacy often react similarly. In nearly each and every case, these were problems of ambiguity – ones where it was not clear what the risks were, and the security (and technology) teams understood the least about the underlying technology and how to manage it’s risks effectively. Organizations that are most effectively managing these risks are those that dedicate resources to experimentation and rapid prototyping to find creative and risk-efficient methodologies for leveraging game-changing technologies while balancing (and hopefully mitigating) risks along the way.
Problem solving is inherently not a technical skill, it is a way of looking at a scenario and breaking it down into smaller problems until you get to the root of the problem. Issues during the problem-solving process usually fall into two buckets: diagnosis, and the devil’s advocate.
The most frequent ask that clients gave me when serving organizations as a consultant was that my clients would ask me to fix a project or deploy a technology when the previous deployment had failed. Often my clients diagnosed the problem incorrectly, and after proper diagnosis we got projects back on track. Full disclosure, I also found this to be the case when I worked in industry as well. Note: RCA means “root cause analysis” and not “causes.” Problems only have one cause and therefore one solution. During RCAs we need to make sure that when multiple problems are identified, that we resist lumping them together. When diagnosed properly, we can label each as a problem of V, U, C, or A.
The second problem is that the devil’s advocate (there is one in every group) will look at VUCA and basically say that there is no way you can prepare for these types of problems without a crystal ball, a generous amount of good luck, or a combination of both. The devil’s advocate often also will scoff at strategic planning and believe that the most effective use of resources is to improve fire fighting skills…after all, that is when heroes are born. The highly technical devil’s advocate will also push back because the prescribed approach does not seem to be a technical solution. In either case, you need to focus in on the problem, diagnose it properly and engage the devil’s advocate to drive the technical solution forward.
Problem solving is a key weapon within the Cyber Governance professional’s arsenal. In order for us to enable decision making and ensure that the most critical problems are being solved…we must diagnose The Four Problems and guide the organization towards a solution. Effective Cyber Governance organizations operate by obliterating oversight, enabling informed decision making, and effectively managing cyber risk. Time for me to get off the soapbox! What did you learn? What do you think? Share, Comment, and Like Below!
Published:
Updated: